FireEye recently posted
a blog article on the compromise of US Veterans of Foreign Wars website, Symantec also has one. I've played with ZXShell in the past and was curious if I could get the DeputyDog/Hidden Lynx actors ZXShell payload working with my command and control server. Turns out you can and I was able to make some interesting comparisons between the client I tested and the vfw dropper.
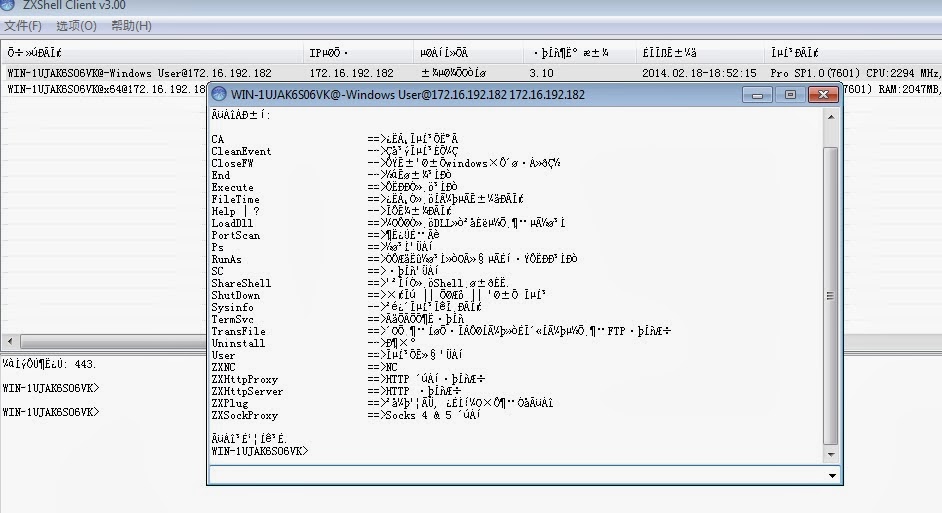
The agent below is the publicly available client and the options available to run on the compromised host (translated descriptions are at the end of this blog).
First thing I noticed was the lack of commands, despite being a newer version (assuming the 3.10 and 3.20 are client versions). Also the descriptions have all been changed to English, which is a bit odd if English isn't your first language. Speaking of odd, I was wondering about this:
In general this is horrible OpSec, if you spend a few minutes looking at it you'll find many examples. Maybe just a case of being lazy or perhaps they were only testing something.
Lots of strangeness with this one but that makes it fun. There is still a lot to dig through but I wanted to post some of my notes while its fresh in my head. If you find anything interesting or something I missed, let me know.
3.10 ZXShell Commands
CA ==> cloning system account CleanEvent -> Clear System Diary CloseFW -> temporarily closed windows comes with a firewall End -> end of the program Execute ==> run a program Time information FileTime ==> clone a file FindPass -> Find a login account password x FindDialPass -> lists all the dial-up account and password x Help | -?> Display the information KeyLog ==> remote computer to capture or record key information x LoadDll ==> load a DLL or inserted into the specified process PortScan ==> port scanning Ps ==> Process Management RunAs ==> to other processes or identity of the user running the program SC ==> Service Management ShareShell ==> Sharing a Shell to others. ShutDown ==> Logout | | restart | | closed system Sysinfo -> View System Details SYNFlood -> SYN attacks x TermSvc ==> Terminal Services Configuration TransFile ==> from the specified URL to download files or upload files to a specified FTP server Uninstall -> uninstall User ==> Account Management System ZXARPS ==> ZXARPS x ZXFtpServer ==> FTP server x ZXNC ==> NC ZXHttpProxy ==> HTTP proxy server ZXHttpServer ==> HTTP server ZXPlug ==> plug-in function, you can add custom commands ZXSockProxy ==> Socks 4 & 5 Proxy The command completed successfully.
And also running VNC from the C2 server:
Dropper calling home to the command and controller server (pcap is from vfw dropper):
Happy hunting.